Report Vulnerability
Product: PIX-LINK
Model: LV-WR07
Vulnerability: Account Takeover - Admin Account
Impact: Account Takeover in the Admin Account.
Author: Red Team ~ Fabrício Oliveira (xf5), Miguel Alves (@0xmupa), Sérgio Charruadas;
PoC
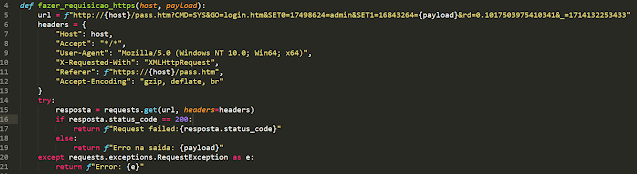
The router has a single account configured as 'admin', making it easier to change the password with an account takeover attack. The vulnerability is observed below by removing the attribute Cookie: Authorization=Basic, which, when removed, still allows the request to be made (beck-end doesn't validate the permission request) allowing to change the Administrator password.
Through this, we can change the Admin password without needing to be authenticated in the session. With this issue, it's allowed to set a new password through the GET Request at var "SET1" resulting in the account takeover.
After this, was crafted an exploit to change Administrador's password.
In the exploit above, there are observed that don't have a 'Cookie: Authorization', and the var 'SET1' receives an input user (the new password value).
In the picture below we look at the usage exploit. The user need only insert the router IP/DNS and the New Password.
As seen below, the exploit has been executed, changing the password to "cwo123".
Follow the video with FULL PoC.


Nenhum comentário:
Postar um comentário